Background and Development of the Purple Code
The Purple Code was an advanced cryptographic system used by the Japanese Imperial Foreign Ministry in the late 1930s. Known in Japanese as the “Type 97 Cipher Machine,” the Purple Code was developed to replace the earlier Red and Blue Codes, providing a higher level of security. It was primarily used to protect Japan’s diplomatic communications, ensuring that crucial information remained confidential.
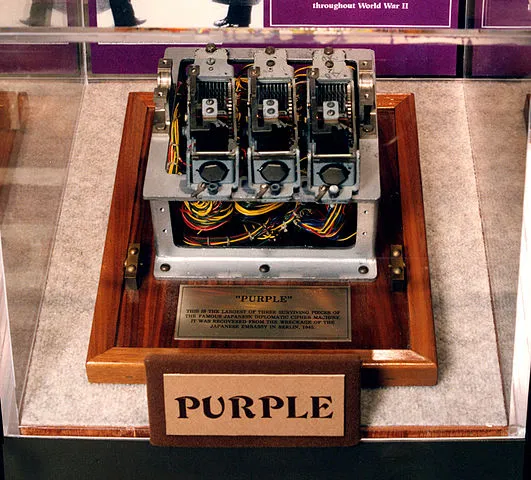
Structure and Operation of the Purple Code
The Purple Code was based on an electromechanical cipher machine with the following characteristics:
- Electromechanical Encryption: The Purple Code used an electromechanical device for encryption. This device employed a rotor mechanism similar to the German Enigma machine but utilized electrical switches to perform more complex transformations.
- Rotor Mechanism: The Purple machine used multiple rotors to transform characters. Each rotor altered the electrical path of the input character, converting it into another character. The rotor settings changed with each message, producing unique ciphertexts and enhancing security.
- Encryption Process: The Purple machine took in 26 characters and converted them through a complex series of electrical paths, resulting in encrypted messages. These encrypted messages were then transmitted via radio or cable.

The American Decryption Effort
The decryption effort was primarily undertaken by the U.S. Signal Intelligence Service (SIS). Key stages in decrypting the Purple Code included:
- Initial Analysis: In 1939, the SIS began intercepting encrypted Japanese diplomatic communications. They started analyzing the new cryptographic system, laying the groundwork for decryption.
- Team Formation: William Friedman, one of the world’s leading cryptanalysts, led the effort. His team included mathematicians and engineers who worked together on the decryption project.
- Reverse Engineering: Friedman and his team embarked on reverse-engineering the Japanese cipher machine. By intercepting and analyzing Japanese diplomatic messages, they constructed a machine similar to the Purple device. This involved understanding the electrical paths and rotor settings to replicate the transformations.
- Successful Decryption: By late 1940, the SIS had successfully built a reverse-engineered machine capable of decrypting the Purple Code. This breakthrough allowed the U.S. to read Japanese diplomatic communications, providing crucial insights into Japan’s diplomatic plans and strategies.
Key Events and Impact of the Purple Code Decryption
- Pre-Pearl Harbor: The decryption of the Purple Code enabled the U.S. to anticipate Japanese diplomatic moves before the attack on Pearl Harbor. Despite gaining valuable insights, the information was not acted upon quickly enough to prevent the attack.
- Wartime Intelligence: Throughout the war, the decryption of the Purple Code provided the Allies with critical information about Japanese diplomatic strategies. This intelligence was vital in securing strategic advantages during the Pacific War. For instance, it allowed the Allies to anticipate Japanese military movements and strategic plans.
- Post-War Impact: The decryption of the Purple Code is a significant achievement in the history of cryptography. It has provided valuable lessons for modern cryptography and information security. It demonstrated the feasibility of decrypting complex cryptographic systems, influencing subsequent cryptographic design and security strategies.
The decryption of the Purple Code was a crucial element in the Allied information-gathering and strategic decision-making processes during World War II. It remains a landmark event in the history of cryptography, offering inspiration and lessons for contemporary information security and cryptographic research.